ACAI ACF Module: terraform-aws-acf-account-cache
GitHub Repository | Terraform Registry
Overview
The terraform-aws-acf-account-cache module deploys a serverless AWS account-context cache. This module enables querying and caching of account-context data from AWS Organizations, storing essential details such as account ID, name, status, tags, and organizational unit (OU) hierarchy.
Cached Account-Context Data
The module retrieves and caches the following details:
{
"accountId": "654654551430",
"accountName": "aws-testbed-core-backup",
"accountStatus": "ACTIVE",
"accountTags": {
"owner": "Platform Security Backup Team"
},
"ouId": "ou-s2bx-wq9eltfy",
"ouIdWithPath": "o-5l2vzue7ku/r-s2bx/ou-s2bx-1rsmt2o1/ou-s2bx-wq9eltfy",
"ouName": "Security",
"ouNameWithPath": "Root/Core/Security",
"ouTags": {
"owner": "Platform Security"
}
}
Key Features
- Deployable in any AWS account within the AWS Organization.
- Supports queries using a structured syntax: Account-Query.
- Optionally provisions the Organization-Info-Reader IAM Role for context cache assumption.
Architecture
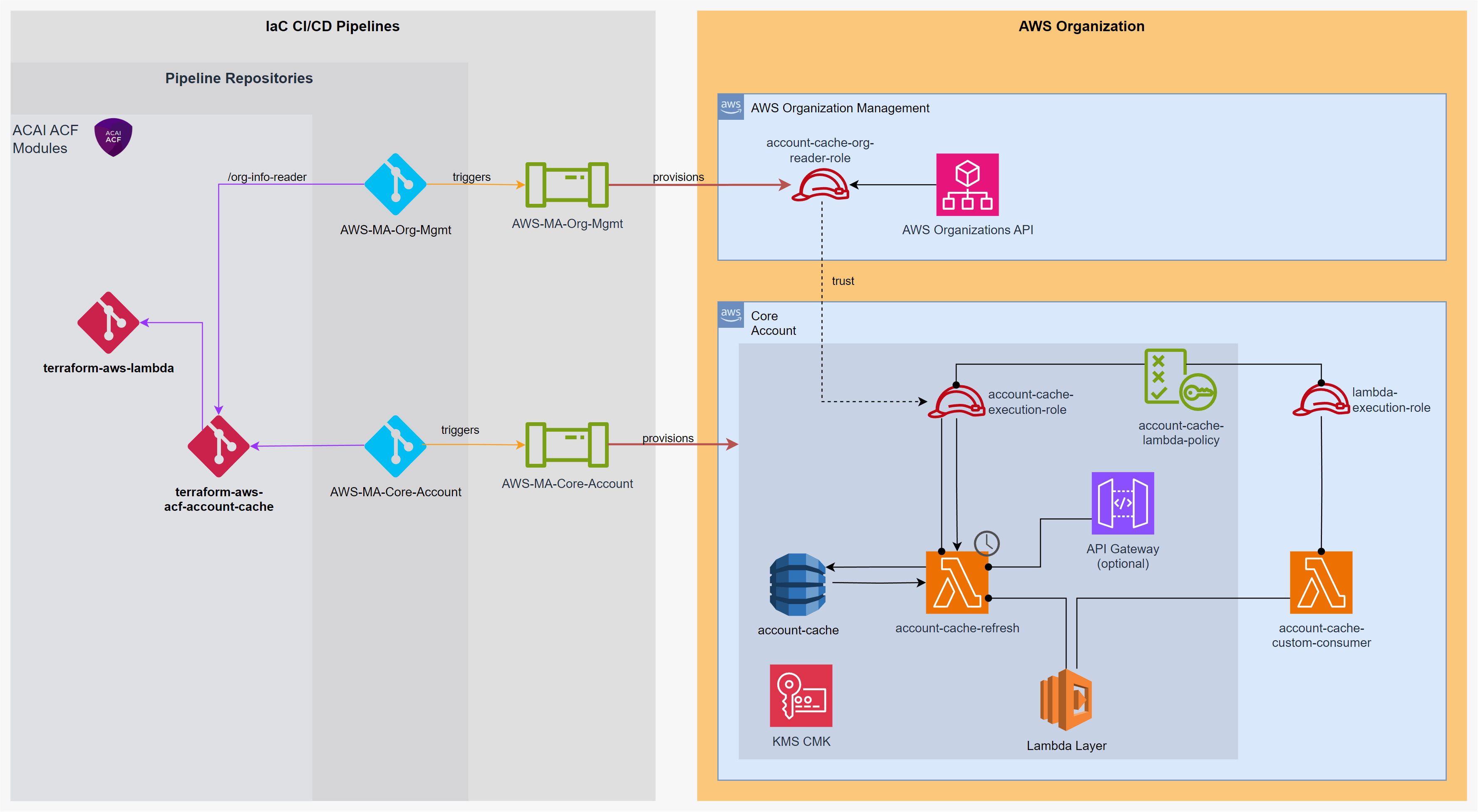
Deploying the Context Cache
module "org_info_reader" {
source = "git::https://github.com/acai-solutions/terraform-aws-acf-account-cache.git//org-info-reader"
settings = {
trusted_account_ids = local.platform_settings.governance.org_mgmt.core_account_ids
}
providers = {
aws = aws.org_mgmt
}
}
module "account_cache" {
source = "git::https://github.com/acai-solutions/terraform-aws-acf-account-cache.git"
settings = {
org_reader_role_arn = module.org_info_reader.iam_role_arn
}
providers = {
aws = aws.core_security
}
}
module "account_cache" {
source = "git::https://github.com/acai-solutions/terraform-aws-acf-account-cache.git//modules/llm-backend"
settings = {
org_reader_role_arn = module.org_info_reader.iam_role_arn
}
providers = {
aws = aws.core_security
}
}
Cache Consumer
Terraform Query Example
data "aws_lambda_invocation" "query_for_prod_accounts" {
function_name = local.platform_settings.governance.account_context_cache.lambda_name
input = <<JSON
{
"query": {
"exclude" : "*",
"forceInclude" : {
"ouNameWithPath" : [
{
"contains": "/Prod/"
}
]
}
}
}
JSON
provider = aws.core_security
}
locals {
prod_accounts = jsondecode(data.aws_lambda_invocation.query_for_prod_accounts.result).result.account_ids
}
AWS Lambda Python Integration
To integrate with AWS Lambda, use the provisioned Context Cache Lambda Layer:
import os
from acai.cache.context_cache import ContextCache
from acai.cache_query.context_cache_query import ContextCacheQuery
import logging
LOGLEVEL = os.environ.get('LOG_LEVEL', 'DEBUG').upper()
logging.getLogger().setLevel(LOGLEVEL)
for noisy_log_source in ["boto3", "botocore", "nose", "s3transfer", "urllib3"]:
logging.getLogger(noisy_log_source).setLevel(logging.WARN)
LOGGER = logging.getLogger()
ORG_READER_ROLE_ARN = os.environ['ORG_READER_ROLE_ARN']
CONTEXT_CACHE_TABLE_NAME = os.environ['CONTEXT_CACHE_TABLE_NAME']
def lambda_handler(event, context):
context_cache = ContextCache(LOGGER, ORG_READER_ROLE_ARN, CONTEXT_CACHE_TABLE_NAME)
context_cache_query = ContextCacheQuery(LOGGER, context_cache)
accounts = context_cache_query.query_cache({
"exclude": "*",
"forceInclude": [
{
"accountTags": {
"environment": "Prod"
},
"ouNameWithPath": [
{
"contains": "/BusinessUnit_1/"
}
]
}
]
})
context_cache.get_member_account_context(accounts[0])