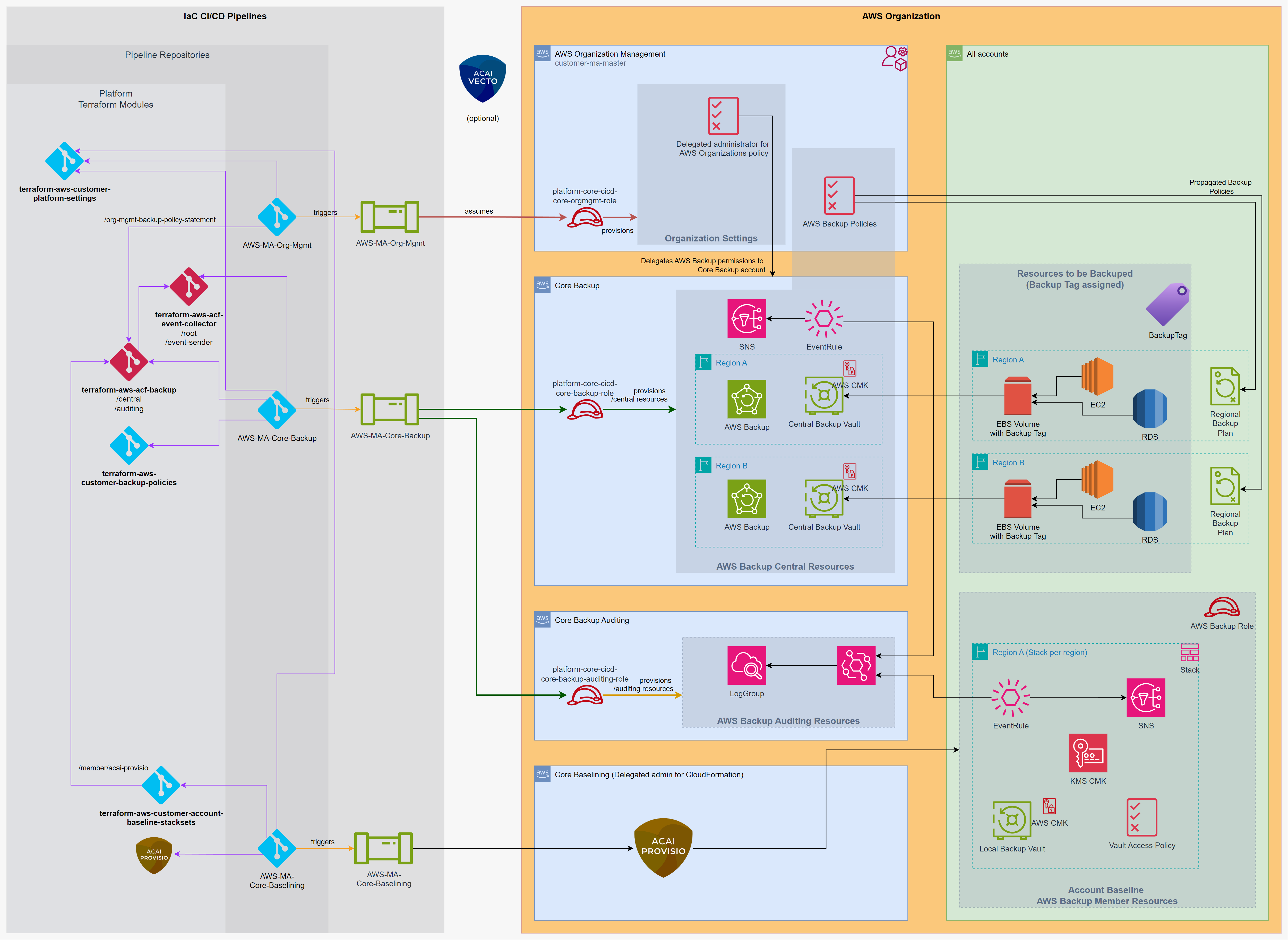
ACAI ACF Module: terraform-aws-acf-backup
Solution
Terraform module to deploy AWS Backup resources in an AWS multi-account environment.
References:
- Data Protection Reference Architectures with AWS Backup
- Guidance for Backup & Recovery on AWS
- AWS centralized-backup-with-aws-backup-and-terraform
- How encryption works in AWS Backup
Recommendation
Ensure AWS Backup is delegated to the designated Core Backup account - use the ACF Module terraform-aws-acf-org-delegation for that task.
Usage
To deploy the ACAI ACF AWS Backup solution, follow these steps:
Specify the AWS Backup Settings
Specify the AWS Backup Settings at a shared place:
locals {
backup_settings = {
auditing = {
eventbus = {
name = "platform--aws-backup--backup-events"
}
}
central_backup = {
account_id = data.aws_caller_identity.current.account_id
vault_name = "platform--aws-backup--core"
kms_cmk = {
alias_name = "alias/platform--aws-backup--core-vault"
}
vault_iam_role = {
name = "platform--aws-backup--role"
}
privileged_principal_arn_list = []
}
account_baseline = {
backup_iam_role_name = "platform--aws-backup--role"
backup_kms_cmk_alias = "platform--aws-backup--cmk"
backup_tag_key = "central_backup"
regional_vault_name = "platform--aws-backup"
sns_topic_name = "platform--aws-backup-failed"
sns_kms_cmk_alias = "platform--aws-backup-sns"
}
}
}
Provisioning AWS Backup Policies
Provision the AWS Backup Policies to the delegated AWS Backup account:
locals {
cron_six_hourly = "cron(0 14 ? * * *)" # task will run at 6:00 AM, 12:00 PM, 6:00 PM, and 12:00 AM UTC every day
cron_daily = "cron(0 14 ? * * *)" # Runs daily at 14:00 UTC
cron_weekly = "cron(0 6 ? * 1 *)" # Runs weekly on Monday at 06:00 UTC
cron_monthly = "cron(0 6 28 * ? *)" # Runs monthly on the 28th day at 06:00 UTC.
backup_policies_rendering_input = {
regions = {
plan_targets = [
"eu-central-1",
"us-east-1"
]
}
policies = [
{
plan_name = "platinum"
policy_title = "plan-platinum"
description = "Platinum backup Plan."
backup_tag_value = "platinum"
backup_start = 60
backup_complete = 240
rules = {
"continuous-backup" = {
retention_period = 32
copy_to_central = false
continuous_backup = true
},
"six-hourly" : {
schedule = local.cron_six_hourly
retention_period = 32
},
"daily" : {
schedule = local.cron_daily
retention_period = 32
},
"monthly" : {
schedule = local.cron_monthly
retention_period = 393
}
}
},
{
plan_name = "gold"
policy_title = "plan-gold"
description = ""
backup_tag_value = "gold"
backup_start = 60
backup_complete = 240
rules = {
"continuous-backup" = {
retention_period = 32
copy_to_central = false
continuous_backup = true
},
"daily" : {
schedule = local.cron_daily
retention_period = 14
},
"weekly" : {
schedule = local.cron_weekly
retention_period = 32
},
"monthly" : {
schedule = local.cron_monthly
retention_period = 393
}
}
},
{
plan_name = "silver"
policy_title = "plan-silver"
description = ""
backup_tag_value = "silver"
backup_start = 60
backup_complete = 240
rules = {
"daily" : {
schedule = local.cron_daily
retention_period = 14
},
"weekly" : {
schedule = local.cron_weekly
retention_period = 32
},
"monthly" : {
schedule = local.cron_monthly
retention_period = 393
}
}
},
{
plan_name = "iron"
policy_title = "plan-iron"
description = ""
backup_tag_value = "iron"
backup_start = 60
backup_complete = 240
rules = {
"daily" : {
schedule = local.cron_daily
retention_period = 9
}
}
}
]
}
}
module "backup_policies_rendering" {
source = "terraform.mycompany.com/acai-consulting/backup/aws//modules/render-policies"
version = "~> 1.0"
backup_settings = local.backup_settings
rendering_input = local.backup_policies_rendering_input
}
Assign the AWS Backup Policies to the target AWS Organization Units or AWS accounts:
locals {
backup_policy_assignments = {
ou_assignments = {
"/root" = [
"platinum-euc1", "platinum-use1",
"gold-euc1", "gold-use1"
]
"/root/CoreAccounts" = [
"platinum-euc1", "platinum-use1",
"gold-euc1", "gold-use1"
]
"/root/WorkloadAccounts" = [
"platinum-euc1", "platinum-use1",
"gold-euc1", "gold-use1"
]
"/root/WorkloadAccounts/BusinessUnit_3" = ["silver-euc1", "silver-use1"]
"/root/WorkloadAccounts/*/Non-Prod" = ["iron-euc1", "iron-use1"]
}
account_assignments = {
"123456789012" = ["silver-euc1", "silver-use1"]
}
}
}
module "backup_policies" {
source = "terraform.mycompany.com/acai-consulting/backup/aws//modules/central-backup-policies"
version = "~> 1.0"
backup_policies = module.backup_policies_rendering.backup_policies
backup_policy_assignments = local.backup_policy_assignments
providers = {
aws = aws.core_backup_euc1
}
}
AWS Backup Central Vault
Deploy the AWS Backup Vaults to the required regions in the Core Backup account:
module "central_backup_primary" {
source = "terraform.mycompany.com/acai-consulting/backup/aws"
version = "~> 1.0"
backup_settings = local.backup_settings
central_vault_trustees = module.backup_policies.central_vault_trustees
providers = {
aws = aws.core_backup_euc1
}
}
module "central_backup_use1" {
source = "terraform.mycompany.com/acai-consulting/backup/aws"
version = "~> 1.0"
backup_settings = local.backup_settings
central_vault_trustees = module.backup_policies.central_vault_trustees
vault_iam_role_arn = module.central_backup_primary.core_configuration_to_write.central_backup.vault_iam_role.arn
providers = {
aws = aws.core_backup_use1
}
}
AWS Backup Member
Deploy the AWS Backup Member resources via ACAI PROVISIO:
Rendered Terraform code:
module "member_acai_provisio_aws_backup" {
source = "terraform.mycompany.com/acai-consulting/backup/aws//member/acai-provisio"
version = "~> 1.2"
provisio_settings = {
provisio_regions = var.platform_settings.governance.org_mgmt
}
backup_settings = local.backup_settings
resource_tags = var.resource_tags
}