ACAI ACF Module: terraform-aws-acf-idc
GitHub Repository | Terraform Registry
Overview
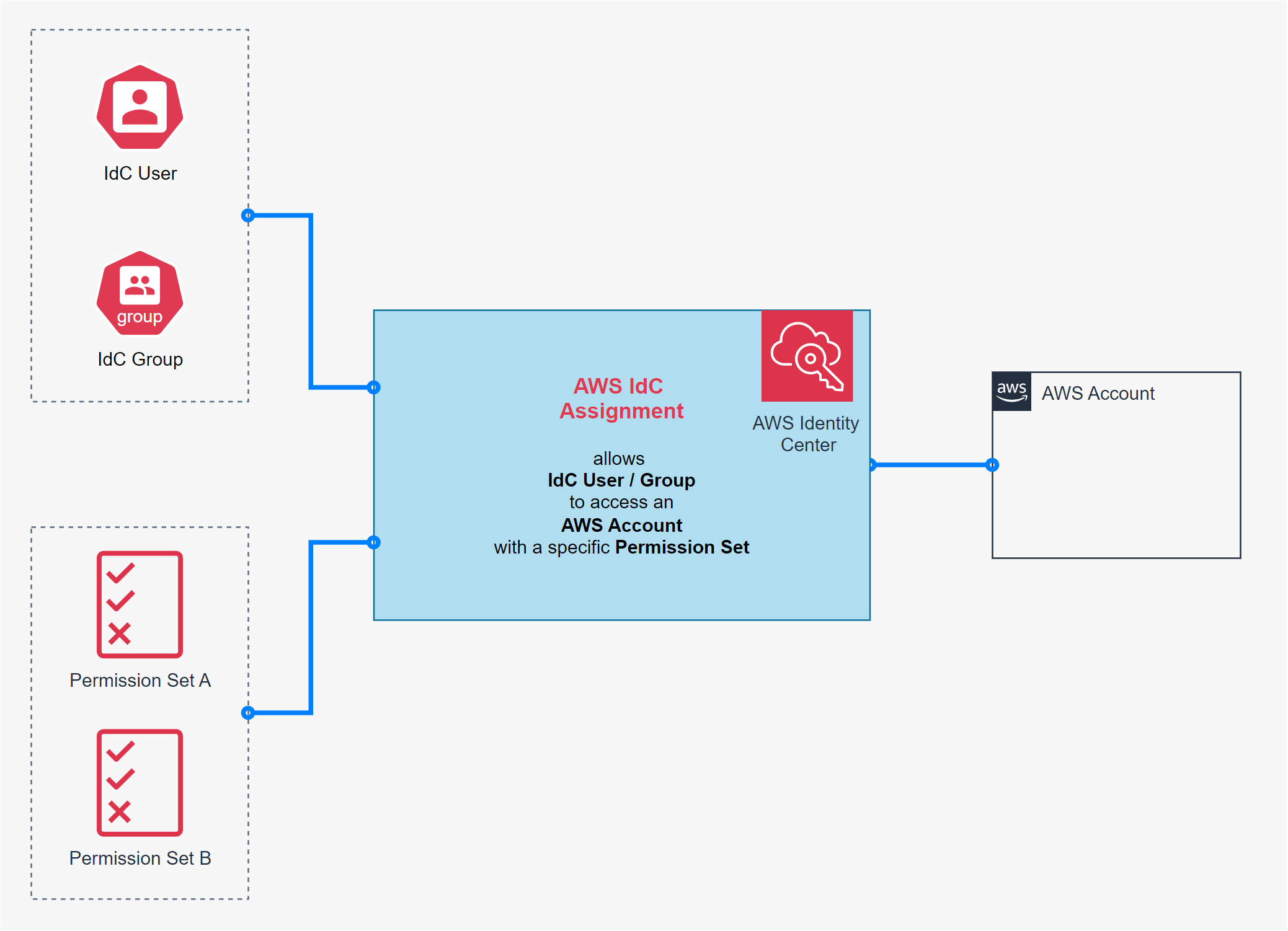
AWS IAM Identity Center (formerly AWS Single Sign-On) simplifies the process of managing access across your AWS Organization by providing a centralized way to handle Single Sign-On (SSO) for users. By using AWS Identity Center, you can efficiently administer access through IdC Assignments, which connect IdC Users or Groups with specific IdC Permission Sets and target AWS accounts [1].
An IdC Permission Set is essentially a template that aggregates one or more IAM policies. This template can include:
- AWS Managed Policies
- Customer Managed Policies
- Inline Policies
- AWS Job Function Policies
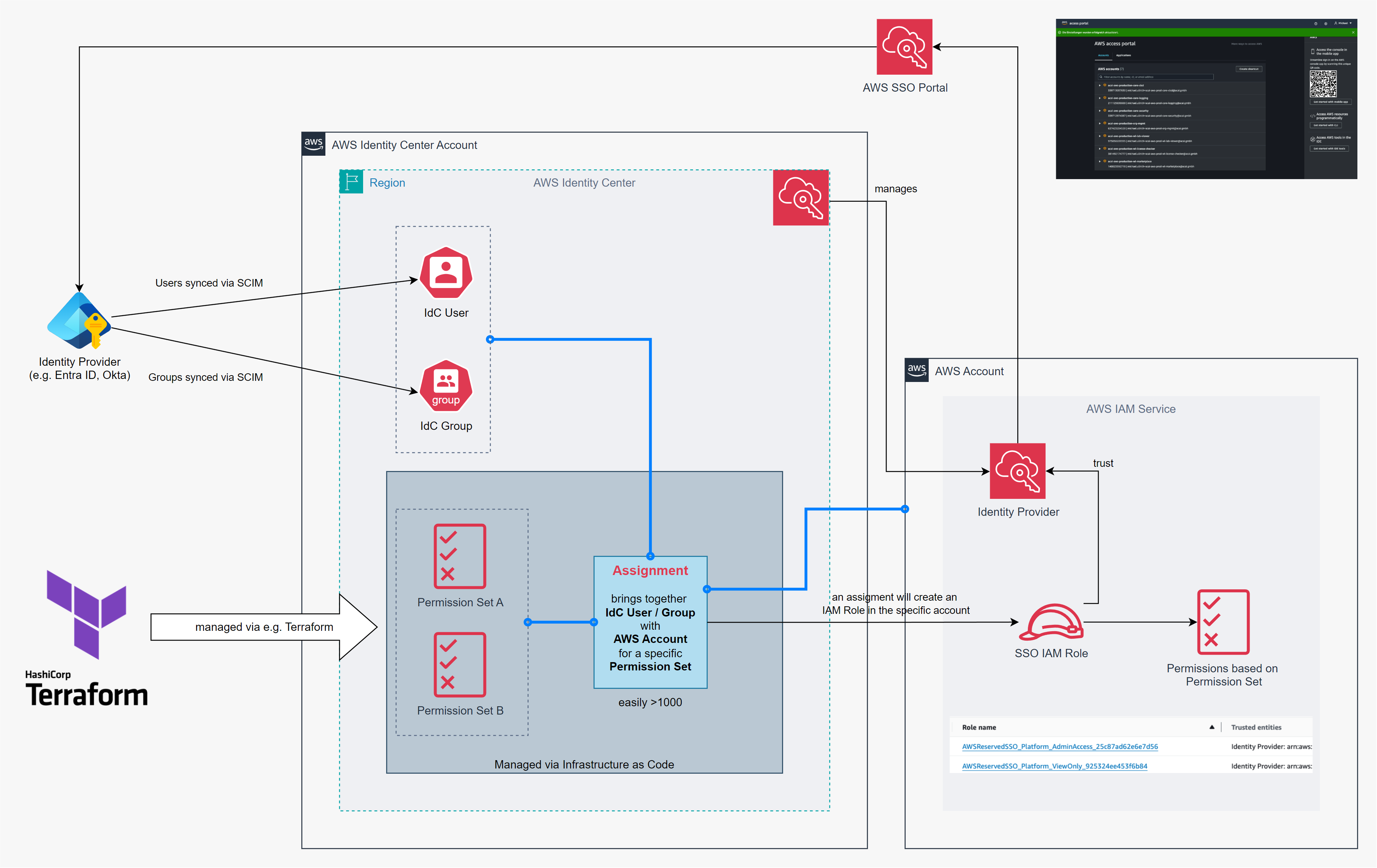
The authentication process for IdC users is typically delegated to an external Identity Provider (IdP) (e.g., Azure Entra ID).
IdC assignments will resolve in IAM Roles in the respective AWS accounts based on the Permissions Sets.
Once authenticated at the IdP, AWS IdC Assignments automatically translate to IAM Roles within the respective AWS accounts, streamlining access control across your organization.
Recommendation
It is advisable to delegate AWS Identity Center management to a dedicated AWS Core SSO Account.
This practice reduces the administrative footprint on the AWS Organization Management Account and enables the application of Service Control Policies (SCPs) to better secure the overall environment.
Solution
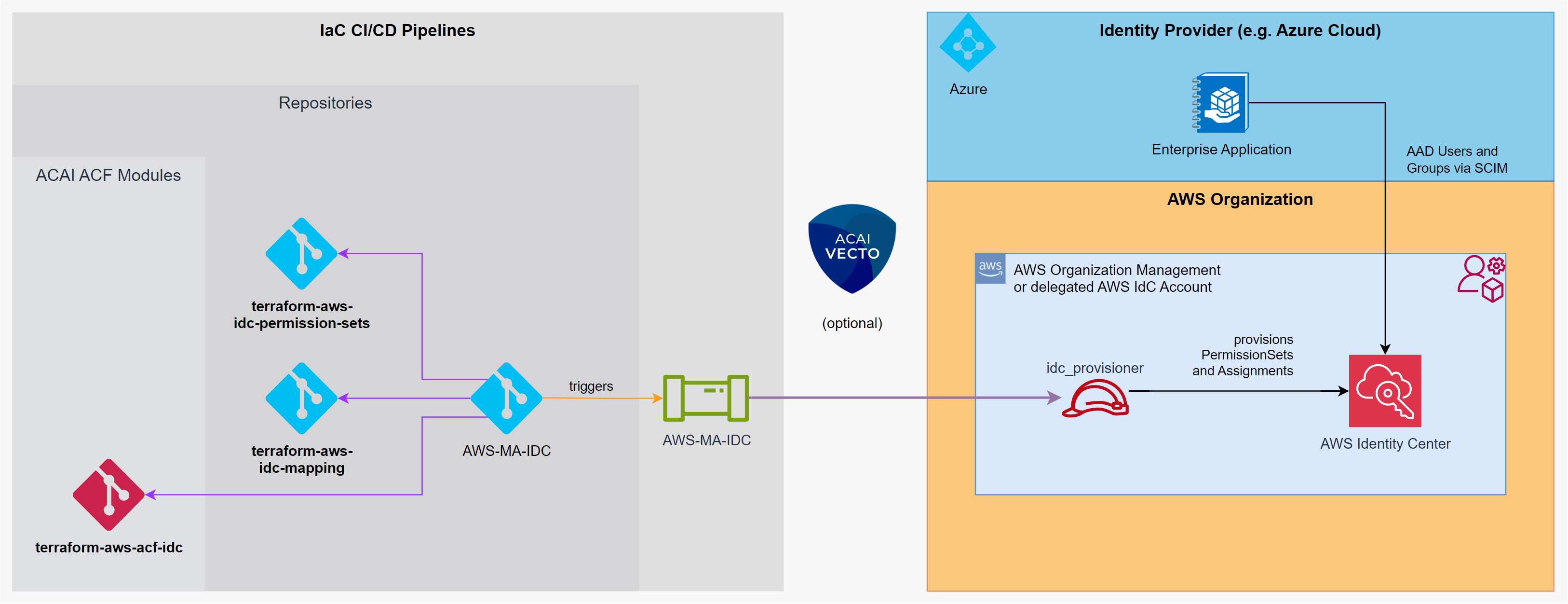
This Terraform module automates the deployment of IAM Identity Center resources to enable Single Sign-On on AWS via an external Identity Provider (e.g. Azure Entra ID).
This module is designed to:
- Provision IdC Permission Sets which act as reusable templates for access policies.
- Configure IdC Assignments that link these Permission Sets to AWS accounts and specific users or groups.
- Facilitate centralized management of identities and permissions, reducing complexity and improving security governance.
Requirements
Please ensure that the following requirements are met
- Enable AWS Organizations and add AWS accounts.
- Enable IAM Identity Center (successor to AWS Single Sign-On).
- Create identities in IAM Identity Center (Users and Groups) or connect to an external identity provider - see documentation.
- Ensure that Terraform pipeline is using a role with permissions required for IAM Identity Center management.
Usage
The module can be configured by defining the IdC Permission Sets and the corresponding AWS account Assignments.
Define IdC Permission Sets:
locals {
permission_sets = [
{
"name" : "Platform_AdminAccess"
"session_duration_in_hours" : 4
"description" : "Used by Platform Admins"
"managed_policies" : [
{
"managed_by" : "aws"
"policy_name" : "AdministratorAccess"
},
]
},
{
"name" : "Platform_ViewOnly"
"session_duration_in_hours" : 4
"description" : "Used by Platform team for view-only access to member accounts"
"managed_policies" : [
{
"managed_by" : "aws"
"policy_name" : "ViewOnlyAccess"
"policy_path" : "/job-function/"
},
{
"managed_by" : "aws"
"policy_name" : "AWSSupportAccess"
},
]
"inline_policy_json" : jsonencode({
"Version" : "2012-10-17",
"Statement" : [
{
"Sid" : "OrganizationsDescribe",
"Effect" : "Allow",
"Action" : [
"organizations:Describe*"
],
"Resource" : [
"*"
]
}
]
})
}
]
}
Specify IdC Assignments:
locals {
account_assignments = [
{
account_id = "992382728088" # ACAI AWS Testbed Core Security Account
permissions = [
{
permission_set_name = "Platform_AdminAccess"
users = ["contact@acai.gmbh"]
}
]
},
{
account_id = "590183833356" # ACAI AWS Testbed Core Logging Account
permissions = [
{
permission_set_name = "Platform_ViewOnly"
users = ["contact@acai.gmbh"]
}
]
}
]
}
Finally, provide the above specifications to the ACF IDC Module: