ACAI SEMPER Documentation
SEMPER Version: >=1.18.0
Introduction
SEMPER streamlines the management of AWS Security Findings through JSON-based policies (JSON).
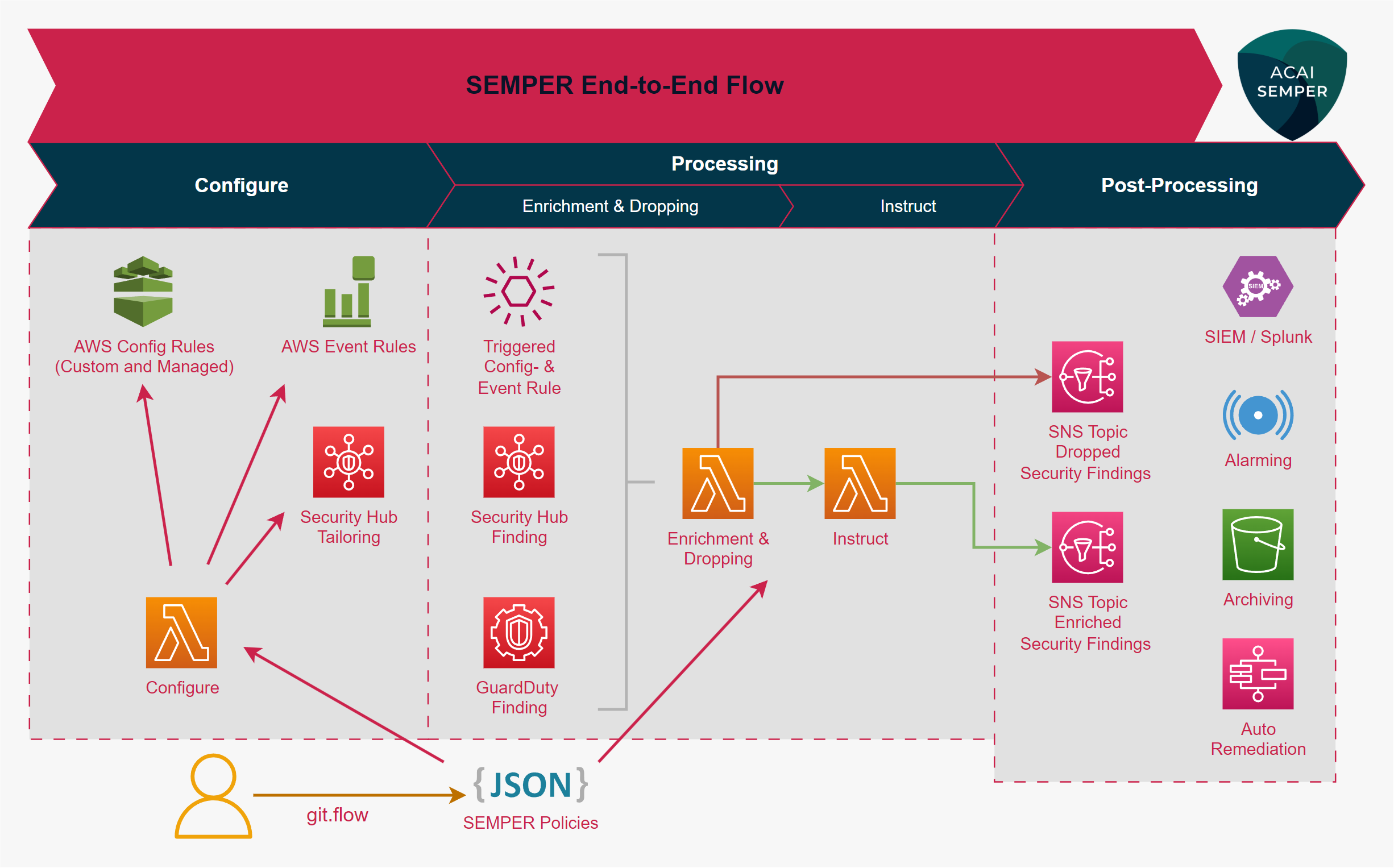
Built for AWS Organizations, SEMPER supports multi-account and multi-region setups. Its workflow is divided into three phases: Configure, Processing, and Post-Processing. All stages are orchestrated via SEMPER Policies, which are maintained as JSON files in the Policy-Repository of the Core Security account. For a detailed description of the policy structure and types, see SEMPER Policies.
Configure
Using a git-flow approach, SEMPER enables the policy-driven provisioning of sensors (AWS Config Rules and AWS Event Rules) and customizes AWS Security Hub Standards and Controls for your AWS accounts.
Processing
Security findings are aggregated and enriched with account context from multiple sources:
- Provisioned sensors (AWS Config Rules, AWS Event Rules from the Configure phase)
- Core AWS Security Hub findings
- Core Amazon GuardDuty findings
Based on SEMPER policies, these enriched findings are either filtered out or further enhanced with instructions for actions such as auto-remediation or monitoring.
Post-Processing
Enriched findings are directed to one of two SNS topics:
- Dropped SNS: For findings that are filtered out.
- Relevant SNS: For findings requiring further action.
Subsequent post-processing steps can include:
- Storing to S3 or CloudWatch
- Forwarding to a SIEM solution
- Triggering alarms
- Initiating auto-remediation
SEMPER Policy-Repository
The SEMPER workflow is entirely policy-driven, handling sensor provisioning and the customization of AWS Security Hub standards and controls. These policies are stored in the SEMPER Policy-Repository within the Core Security account and are categorized into different types:
The repository adheres to a strict folder structure with one JSON file per policy. In directories marked with "…", you can add your own JSON policies—just ensure they are placed in the correct folder based on their type. To disable a policy, simply move the JSON file into a subfolder (e.g., /disabled).
SEMPER Policy-Repository
├───10_configure/
│ ├───config_rules/
│ │ ├── configure_config_rule_policy1.json
│ │ ├── configure_config_rule_policy2.json
│ │ └── ...
│ ├───disabled/
│ │ ├── disabled_policy.json
│ │ └── ...
│ ├───event_rules/
│ │ ├── configure_event_rule_policy1.json
│ │ ├── configure_event_rule_policy2.json
│ │ └── ...
│ └───securityhub/
│ ├───10_controls/
│ │ ├── sh_control1.json
│ │ ├── sh_control2.json
│ │ └── ...
│ ├───20_standards/
│ │ ├── sh_standards.json
│ │ └── ...
│ └───30_standard_controls/
│ ├── sh_standard_control1.json
│ ├── sh_standard_control2.json
│ └── ...
├───20_filtering/
│ ├───cloudtrail_api_calls/
│ │ ├── api_call_filter_policy1.json
│ │ ├── api_call_filter_policy2.json
│ │ └── ...
│ ├───guardduty_findings/
│ │ ├── gd_filter_policy1.json
│ │ └── ...
│ └───securityhub_findings/
│ ├── sh_filter_policy1.json
│ ├── sh_filter_policy2.json
│ └── ...
└───30_extension/
├── extension_policy1.json
├── extension_policy2.json
└── ...