SEMPER Policy Documentation
Required Semper Version: >=1.18.0
SEMPER Policy Elements
Every SEMPER Policy follows this standard structure:
{
"metaData": {...},
"configure" | "filtering" | "extension": {
"policyScope": <policyScopePattern>,
...
<typeSpecificSection>
...
},
"auditing": {...}
}
| Key | Value-Type | Description |
|---|---|---|
metaData |
object | Optional but recommended. Provides attributes to organize your policies (e.g., versioning, title, description, policy-type, ownership). |
configure or filtering or extension |
object | Determines the type of SEMPER policy. Only one of these should be present. |
.policyScope |
object | Optional. Defines where the policy applies (accounts and regions). |
.<typeSpecificSection> |
object | Contains policy-type specific configurations. |
auditing |
object | Optional but recommended. Provides attributes for policy auditing (e.g., lastAttestationDate, auditor contact details). |
Policy Syntax
The SEMPER policy syntax is described in detail on this page.
Policy Scope Configuration
You can precisely specify which member accounts and AWS regions a SEMPER policy should apply to.
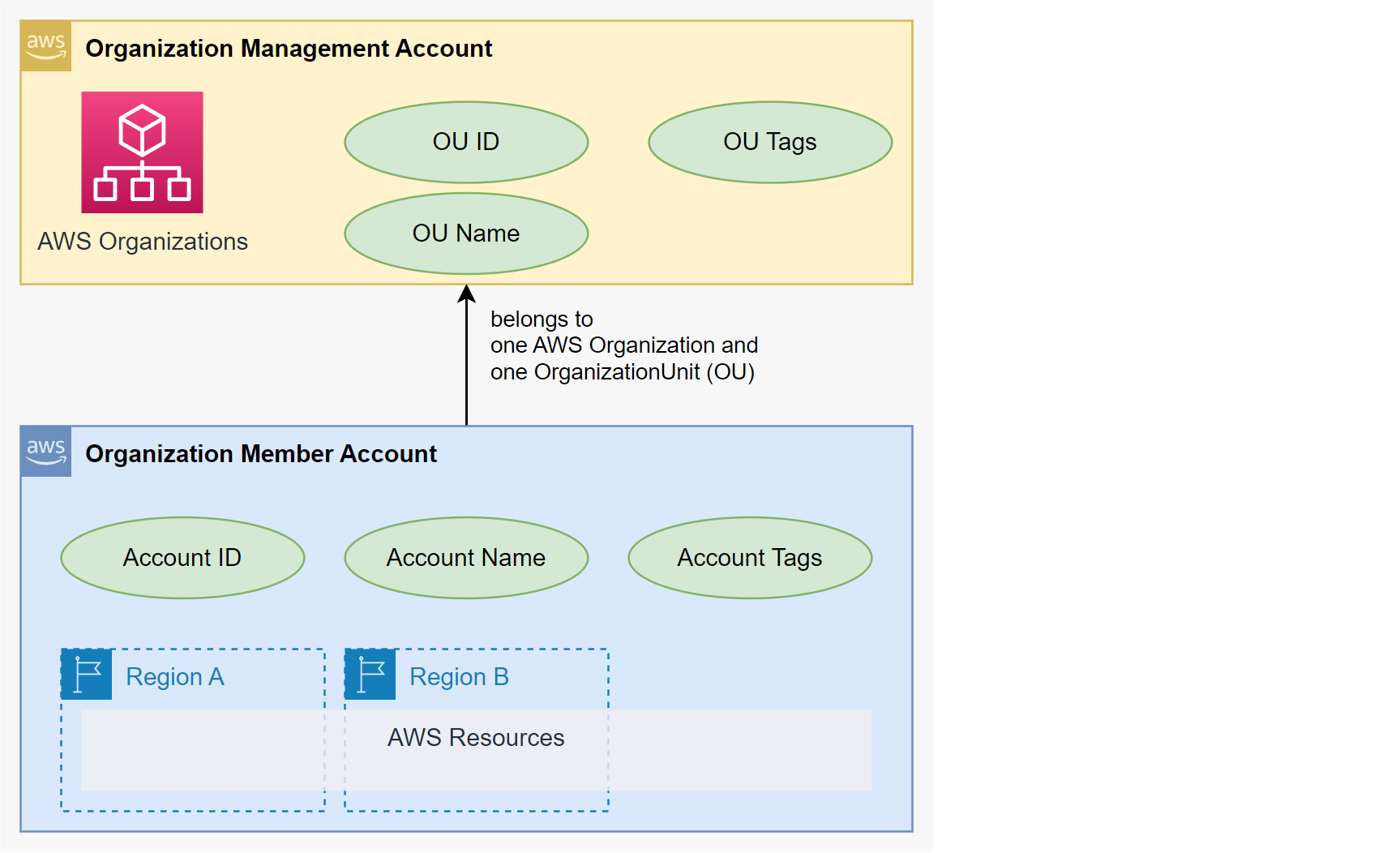
Account Attributes
An AWS account has the following attributes:
{
"accountAttibutes": {
"accountId": "string",
"accountName": "string",
"accountStatus": "string",
"accountTags": {
"key1": "value1",
"key2": "value2"
},
"ouId": "string",
"ouIdWithPath": "string",
"ouName": "string",
"ouNameWithPath": "string",
"ouTags": {
"key1": "value1",
"key2": "value2"
}
}
}
PolicyScope Structure
The policyScope section allows you to define:
- Account scope: Based on AWS account and Organization Unit (OU) properties
- Region scope: Based on AWS region codes
{
"policyScope": {
"accountScope": <accountScope> | [<accountScopePattern>, <accountScopePattern>, ...],
"regionScope": 'string' | ['string'] | <regionScopePattern>
}
}
| Key | Value-Type | Description |
|---|---|---|
policyScope |
object | (optional) will limit the scope of the policy to specific accounts and regions |
.accountScope |
object | Optional. See Account Scope Configuration |
.regionScope |
object | Optional. See Region Scope Configuration |
Account Scope Configuration
Account scope is defined using a pattern that follows an exclude-then-include approach (similar to how rsync excludes and includes files):
{
"accountScope": {
"exclude": "*" | <AccountAttributesPattern> | [<AccountAttributesPattern>, <AccountAttributesPattern>, ...],
"forceInclude": <AccountAttributesPattern> | [<AccountAttributesPattern>, <AccountAttributesPattern>, ...]
}
}
| Key | Value-Type | Description |
|---|---|---|
.exclude |
"*" or JSON-Pattern or List of JSON-Patterns |
Optional. AccountAttribute-Patterns for accounts to exclude |
.forceInclude |
JSON-Pattern or List of JSON-Patterns | Optional. AccountAttribute-Patterns for accounts to force-include |
Example 1: Account Tag Filtering
Include only accounts with tag "AccountName" starting with "Core":
{
"policyScope": {
"accountScope": {
"exclude": "*",
"forceInclude": {
"accountTags": {
"AccountName": [
{
"prefix": "Core"
}
]
}
}
}
}
}
Example 2: Environment Exclusion
Two equivalent ways to exclude production environments:
Example 3: OU-Path Filtering
All accounts with account-tag environment = "Prod" and that have "/BusinessUnit_1/" in their OU-path:
{
"policyScope": {
"accountScope": {
"exclude": "*",
"forceInclude": [
{
"accountTags": {
"environment": "Prod"
},
"ouNameWithPath": [
{
"contains": "/BusinessUnit_1/"
}
]
}
]
}
}
}
Region Scope Configuration
The regionScope section allows you to override target regions using AWS region names:
{
"regionScope": {
"exclude": "*" | 'string' | ['string'],
"forceInclude": 'string' | ['string']
}
}
| Key | Value-Type | Description |
|---|---|---|
regionScope |
object | Optional. First evaluates exclude, then forceInclude |
.exclude |
"*" or array of strings |
Optional. Elements evaluated with logical OR |
.forceInclude |
array of strings | Optional. Elements evaluated with logical OR |
Example 1: Region-Specific Policy
Exclude all regions except "us-east-1":
Combined Examples
Example 1
Requirement: Provision Event-Rule to us-east-1 in selected accounts with "Environment" = "Prod" Default AWS Regions: eu-central-1, us-east-2
{
"policyScope": {
"accountScope": {
"exclude": "*",
"forceInclude": {
"accountTags": {
"environment": "Prod"
}
}
},
"regionScope": {
"exclude": "*",
"forceInclude": [
"us-east-1"
]
}
}
}
Example 2
Requirement: Provision Event-Rule to default AWS regions and us-east-1 in selected accounts on OU = "BusinessUnit_1" or where "AccountName" starts with "Core-" Default AWS Regions: eu-central-1, us-east-2