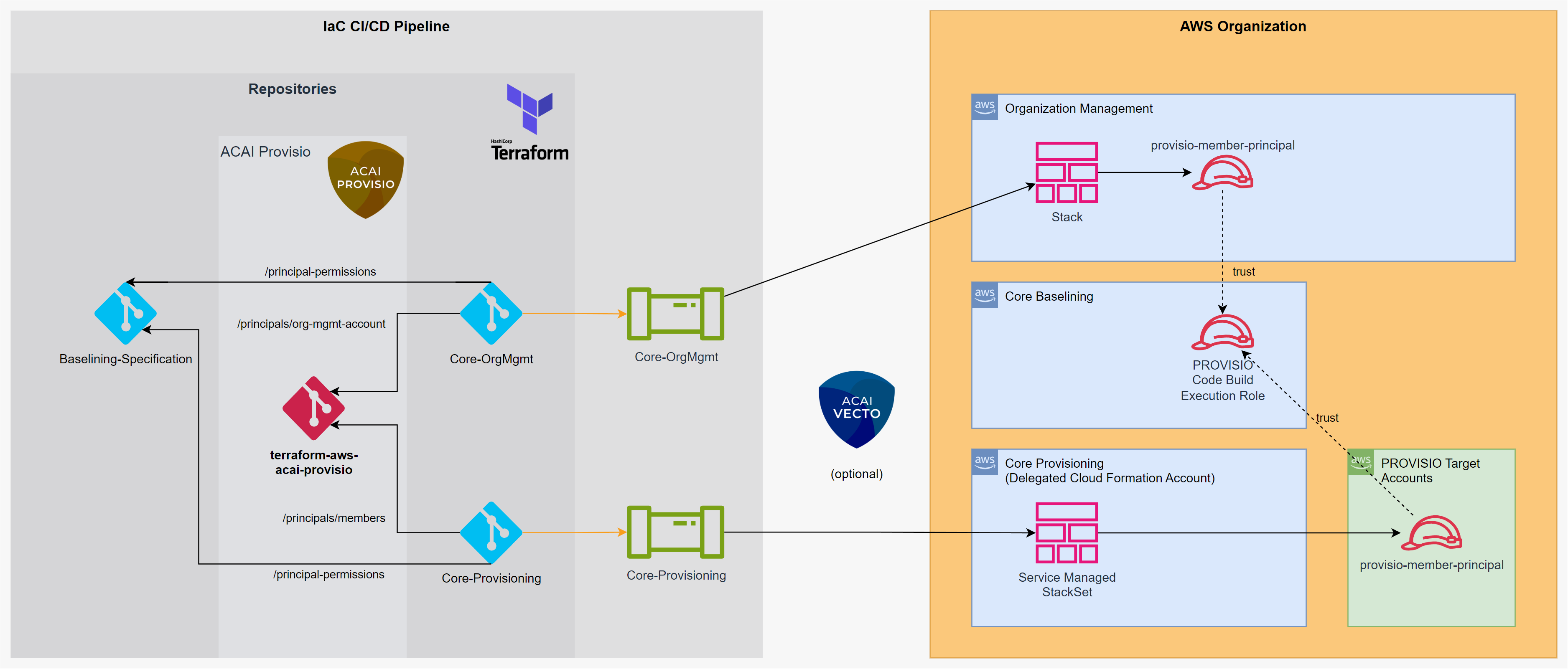
ACAI PROVISIO Deployment
PROVISIO Version: 1.3.0
Duration: 1 hour
The PROVISIO solution consists of two components:
- /core - The core solution deployed to the designated Core Baselining account.
- /org-mgmt/member-principal and /member-principal - The baselining principals deployed to all member accounts.
Prerequisites
- Select one AWS account of your AWS Organization as the Core Baselining account to deploy the PROVISIO core solution
- Select one AWS account that is delegated administrator for CloudFormation or nominate the Core Baselining account to deploy the PROVISIO member principal solution
- Ensure that the acai-account-cache-org-reader-role is available in the AWS Organization Management Account.
Deploy Core Solution
Deploy the PROVISIO Core Solution to the selected Platform Core Baselining account.
Terraform Configuration
module "provisio_account_cache" {
source = "git::https://github.com/acai-consulting/terraform-aws-acf-account-cache?ref=1.3.0"
settings = {
org_reader_role_arn = "arn:aws:iam::123456789012:role/acai-account-cache-org-reader-role"
}
providers = {
aws = aws.core_baselining
}
}
module "provisio_core" {
source = "git::https://github.com/acai-consulting/terraform-aws-acai-provisio//core?ref=1.0.0"
provisio_settings = {
org_reader_role_arn = local.platform_settings.governance.org_mgmt.org_info_reader.iam_role_arn
core_provisio = {
account_cache = {
existing_ddb_name = module.provisio_account_cache.ddb_name
existing_permission_policy_arn = module.provisio_account_cache.cache_lambda_permission_policy_arn
}
}
member_principal = local.platform_settings.governance.provisio.member_principal
}
provisio_baselining_specification = {
terraform_version = "1.5.7"
provider_aws_version = "5.75.0"
provisio_regions = local.platform_settings.governance.org_mgmt
}
providers = {
aws = aws.core_baselining
}
}
Store the output module.provisio_core.provisio_configuration_to_write in the Platform Configuration Store using the terraform-aws-acf-core-configuration module.
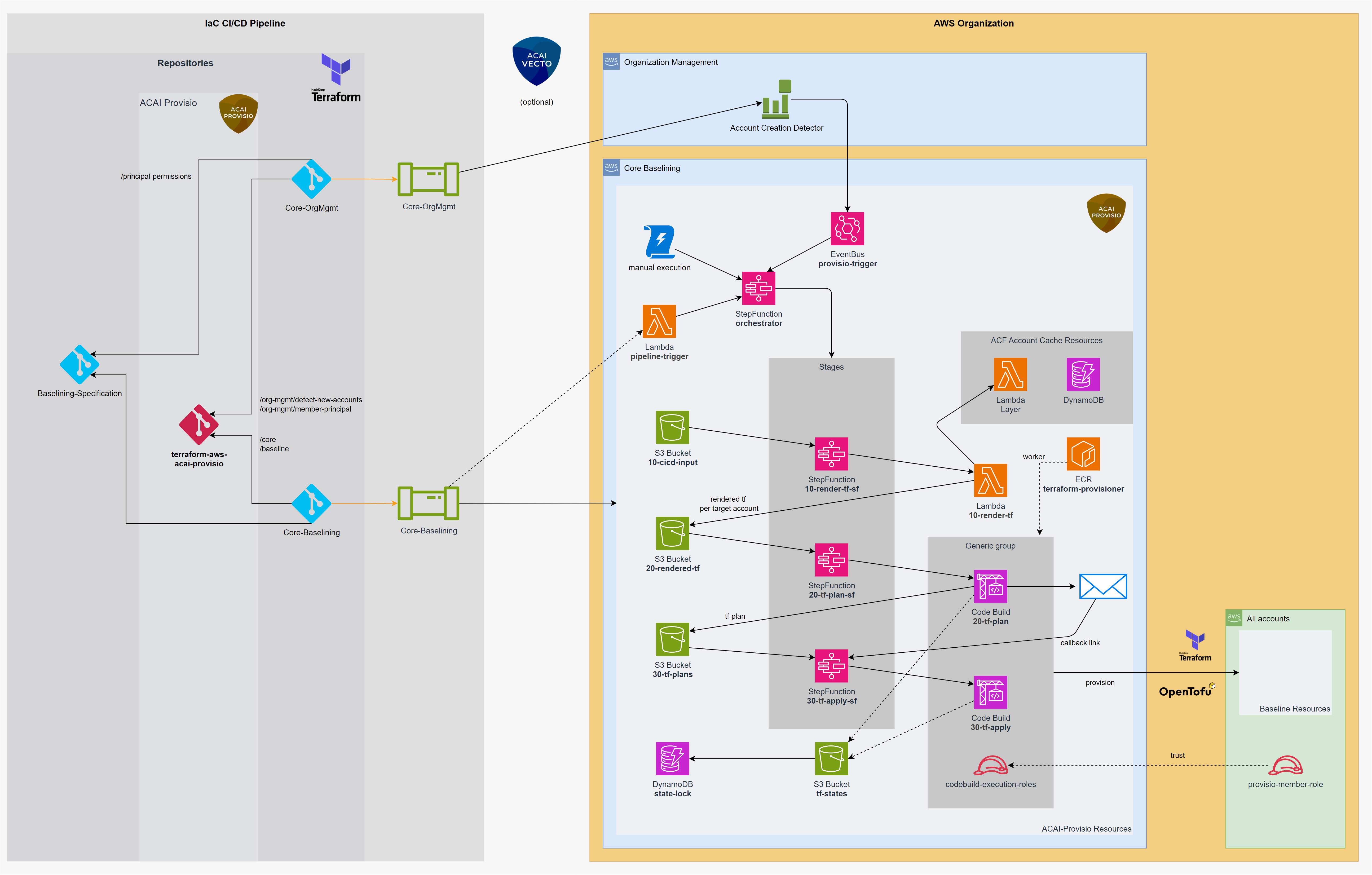
Deploy Principals
The PROVISIO Principal IAM Role must be deployed in all member accounts to be baselined. This role must trust the CodeBuild Execution Role of the PROVISIO Core Solution. Provide the ARN of the CodeBuild Execution Role to provisio_settings.member_principal.iam_role.trustee.
For the AWS Organization Management Account, an AWS CloudFormation Stack will be used. For all other AWS accounts, a ServiceManaged AWS CloudFormation StackSet will be deployed.
locals {
provisio_settings = module.platform_settings.governance.provisio
}
module "acai_provisio_member_permissions" {
source = "git::https://github.com/acai-consulting/terraform-aws-account-baseline//member-permissions?ref=1.0.0"
}
module "provisio_member" {
source = "git::https://github.com/acai-consulting/terraform-aws-acai-provisio//org-mgmt/member-principal?ref=1.0.0"
provisio_member_principal = {
iam_role = merge(
local.platform_settings.governance.provisio.member_principal.iam_role,
{
rendered_permissions = module.acai_provisio_member_permissions.cf_permissions_rendered
}
)
}
resource_tags = local.resource_tags
providers = {
aws = aws.aws_org_mgmt
}
}
locals {
provisio_settings = module.platform_settings.governance.provisio
}
module "acai_provisio_member_permissions" {
source = "git::https://github.com/acai-consulting/terraform-aws-account-baseline//member-permissions?ref=1.0.0"
}
module "provisio_member" {
source = "git::https://github.com/acai-consulting/terraform-aws-acai-provisio//member-principal?ref=1.0.0"
provisio_settings = {
central_stackset = {
name = local.provisio_settings.central_stackset.name
member_principal_target_ou_id = local.provisio_settings.central_stackset.member_principal_target_ou_id
call_as = "DELEGATED_ADMIN"
}
member_principal = {
iam_role = merge(
local.provisio_settings.member_principal.iam_role,
{
rendered_permissions = module.acai_provisio_member_permissions.cf_permissions_rendered
}
)
}
}
resource_tags = local.resource_tags
providers = {
aws = aws.delegated_cloudformation
}
}